Boot.dev Blog - Pg. 12


The Nuances of Constants in Go; Go Isn't JavaScript
Oct 22, 2020 by Lane WagnerConstants can be confusing and easy to misuse in Go if you are coming from an untyped language. Let’s take a look at some of the nuanced details of how they work in Go. It’s probably unsurprising, but Go’s constants are almost nothing like JavaScript’s bastardized version of the concept.


6 Things to Avoid When Contributing to Open-Source Projects
Oct 21, 2020 by Lane WagnerWith #HacktoberFest being a thing, there has been an influx of devs desperately trying to contribute to their favorite Open-Source projects. Unfortunately, many of these pull requests have been a waste of time, with the maintainers ultimately unable to use the contributions. Maintainers don’t want to waste their time reviewing bad PRs, and contributors don’t want to waste their time writing code that will never make it into production.
Functional Programming Course Released
Oct 19, 2020 by Lane WagnerWe just launched our new “Learn Functional Programming” course, and frankly, I’m a bit exhausted (more on that later). This course is an interactive code-in-the-browser course that teaches the basics of FP in JavaScript and PureScript.

How To Correctly Validate Passwords - Most Websites Do It Wrong
Oct 15, 2020 by Lane WagnerYou’ve probably visited a site and attempted to sign-up only to be met with errors such as:


6 Tips for Hiring Developers
Oct 13, 2020 by Lane WagnerSo you want to hire a developer? Or maybe you just want to know what is going through the heads of employers like myself. Either way, let’s dive right into what I think are best practices for hiring programmers. I’ve found my opinions to be quite controversial, but I do put them into practice in my own career and at boot.dev. When you inevitably disagree with some of my points, feel free to @ me.


Running Rust in the Browser with Web Assembly
Oct 12, 2020 by Lane WagnerI’ve recently been working on getting Rust support in the boot.dev app. To write a more engaging course, I want students to be able to write and execute code right in the browser. As I’ve learned from my previous posts on this topic, the easiest way to sandbox code execution on a server is to not execute code on a server. Enter Web Assembly, stage left.


Top 4 Coding Languages To Learn For Beginners in 2022
Oct 07, 2020 by Lane WagnerCoding languages, tools, and frameworks are in a constant state of flux, improvement, deprecation, and popularity swings. Let’s take a look at the top 4 languages for new programmers to learn in 2021.


Education's Shameful State of the Art
Oct 05, 2020 by Lane WagnerHigher education had its problems before Covid-19. Now the crippling inefficiencies, backbreaking cost, and lack of alternatives are being forced into the spotlight. We’re working on what will eventually grow into the alternative to overpriced universities and ineffective Bootcamps at boot.dev. In the meantime, let’s take a look at education’s biggest problems, and how we can solve them.


How to Structure a Golang Project
Oct 01, 2020 by Lane WagnerI lead a team that’s responsible for anywhere from 15-25 Go microservices at any given time. We’re constantly creating new services and libraries, so it’s become important to streamline the project creation process. I’m mostly writing this article for myself as a kind of self-documentation, but hopefully, you’ll find it useful as you create new Go projects for yourself.


What Is Entropy In Cryptography?
Sep 28, 2020 by Lane WagnerIf you’re familiar with the laws of thermodynamics, you may recognize the second law as the one that deals with entropy. In the realm of physics, entropy represents the degree of disorder in a system. Because systems tend to degrade over time, thermodynamic energy becomes less available to do mechanical work.


How to Make a Simple Vue Custom Select Component
Sep 25, 2020 by Lane WagnerCreating a custom select tag with its own styling is notoriously difficult. Sometimes it’s impossible to build from scratch without a combination of styled divs and custom JavaScript. In this article, you’ll learn how to create a custom select component in Vue that can be easily styled with your own CSS. In fact, it’s the same component we use in production on boot.dev, and you can see it in action on our JavaScript playground.


Running Python in the Browser with Web Assembly
Sep 24, 2020 by Lane WagnerI’ve been wanting to expand boot.dev’s curriculum, and one of the most requested programming languages has been Python. Because my courses allow students to write and execute code right in the web browser, I decided to look into existing projects that allow a Python interpreter to run in the browser using Web Assembly. I settled on a tool called Pyodide, which does just that.


Running Go in the Browser with WASM and Web Workers
Sep 23, 2020 by Lane WagnerWe’ve recently made big changes to how we execute Go in the browser on boot.dev and want to explain the enhancements. Web Workers are the reason we’ve been able to solve some of the serious browser-related coding problems that were holding us back. Consider this article a sequel to Running Go in the Browser with Web Assembly.


Practical Patterns for Technical Writing
Sep 22, 2020 by Ben BartenWriting technical documents like API or architectural documentation which exceeds a simple flow diagram can be a daunting task. If you have some experience with technical documents, you will probably agree that there is nothing more frustrating than bad documentation.
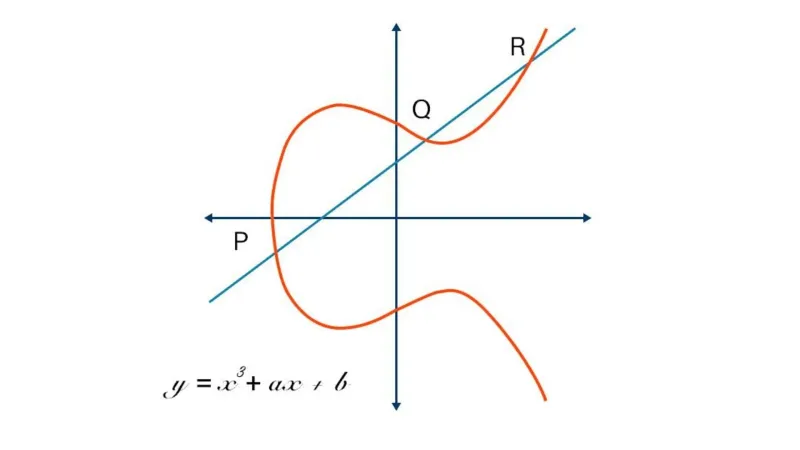

Elliptic Curve Cryptography: A Basic Introduction
Sep 17, 2020 by Lane WagnerElliptic Curve Cryptography (ECC) is a modern public-key encryption technique famous for being smaller, faster, and more efficient than incumbents. Bitcoin, for example, uses ECC as its asymmetric cryptosystem because it is so lightweight. The mathematical entity that makes all of this possible is the elliptic curve, so read on to learn how these curves enable some of the most advanced cryptography in the world.
"Learn Algorithms" Course Released
Sep 14, 2020 by Lane WagnerWe’ve launched our new Data Structures and Algorithms course! We wrote this course for engineers who need a refresher on computer science basics or want to learn the fundamentals for the first time.


Is AES-256 Quantum Resistant?
Sep 10, 2020 by Lane WagnerWith quantum computers getting more powerful each year, many worry about the safety of modern encryption standards. As quantum computers improve in performance and the number of qubits used for calculations increases, current cryptosystems are under threat. AES-256 is one of the most powerful symmetric ciphers, but will it remain secure in a post-quantum world?


How to Make Pure Functions in Golang
Sep 07, 2020 by Lane WagnerPure functions are often hyped up in the JavaScript world, probably because of the abundance of stateful front end applications. While pure functions have their downsides (i.e. inconvenience, potentially large argument lists), they should be used as much as reasonably possible.

Guard Clauses - How to Clean up Conditionals
Sep 06, 2020 by Lane WagnerOne of the first concepts new developers learn is the if/else statement. If/else statements are the most common way to execute conditional logic. However, complex and nested if/else statements can quickly become a cognitive burden and compromise the readability of a program.


Create a Golang Video Streaming Server Using HLS
Sep 04, 2020 by Lane WagnerIn this tutorial, we’ll go step-by-step through building a video streaming API (which will work for music as well) in Go. Don’t worry, it’s surprisingly easy to build a robust media streaming server, especially if we utilize a modern communication protocol, HLS.


Should You Return Empty or Nil Slices in Go?
Sep 03, 2020 by Lane WagnerIn Go, we often need to return zero values. Idiomatic Go encourages the use of guard clauses, and guard clauses necessitate the need to return early. When returning early with an error, by convention all other return values should be zero values. The confusion arises with data types like maps and slices. Should maps and slices be returned as a simple nil value, or should an empty but instantiated value be returned?


Slow Is Smooth, Smooth Is Fast - 25% of Our Time Refactoring
Sep 01, 2020 by Lane WagnerMy team has been spending less of our “free” time working on bugs and features from the backlog, and more time refactoring our code and tests. As a result, and perhaps somewhat counterintuitively, we’ve noticed a significant increase in our throughput of features and bug fixes.


Top 15 Golang Interview Questions [Updated 2024]
Aug 31, 2020 by Lane WagnerLet’s take a look at some good technical questions to be familiar with, whether you are looking to nail your next Golang interview, or if you’re the interviewer yourself..

Creating a Custom Tooltip Component in Vue
Aug 28, 2020 by Lane WagnerThere are plenty of libraries out there that will have you up and running with a good tooltip solution in minutes. However, if you are like me, you are sick and tired of giant dependency trees that have the distinct possibility of breaking at any time. For that reason, we’re going to build a custom single file tooltip component that you can build yourself and tweak to your heart’s content. It might take 15 minutes instead of 3… sorry about that.


Bcrypt Step by Step
Aug 24, 2020 by Lane WagnerBcrypt is a key derivation function, which can be thought of as a special kind of hash function. Its purpose is to slowly convert a piece of input data to a fixed-size, deterministic, and unpredictable output. A common use case is to convert a password into an n-bit cryptographic key, which can then be used for safe authentication.