PGP, or its open-source alternative, GPG, is a program used to encrypt data such that only an authorized party can decrypt it. In this introduction, we will cover its use-cases and a high-level overview of the algorithms involved.
Both programs (and others) adhere to the OpenPGP protocol. Because it is an implementation agnostic protocol, people can use the software they are most comfortable with and still send secure messages to each other.
Only Pretty Good? 🔗
The “pretty good” part of “Pretty Good Privacy” is a hilarious understatement. It uses secure building blocks and remains an extremely private (albeit not very user-friendly) protocol for secure communication.
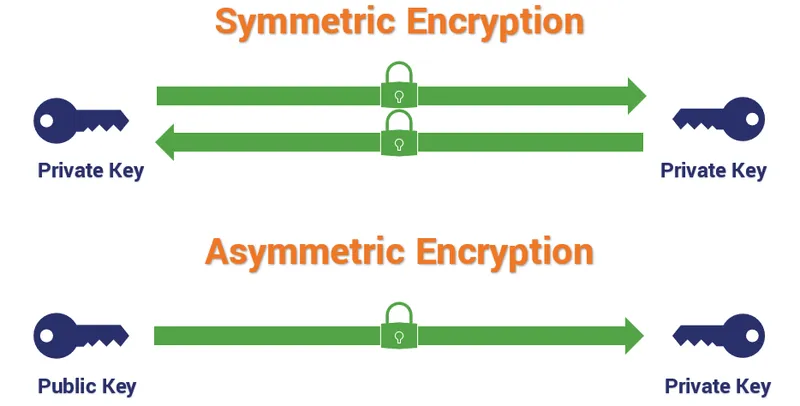
Symmetric vs Asymmetric Encryption 🔗
Asymmetric algorithms allows users to communicate securely without sharing private keys. They are suitable for the encryption of messages meant to be sent over an untrusted medium like emails or text messages.
Symmetric algorithms are computationally fast. They are primarily used to encrypt data at rest, such as files on a hard drive.
PGP is a hybrid cryptosystem, it takes advantage of certain benefits from symmetric and asymmetric systems. PGP uses asymmetric keys to encrypt symmetric keys, which are used to encrypt messages. This keeps PGP computationally efficient while also allowing users to own their own private keys.
How Does It Work? 🔗
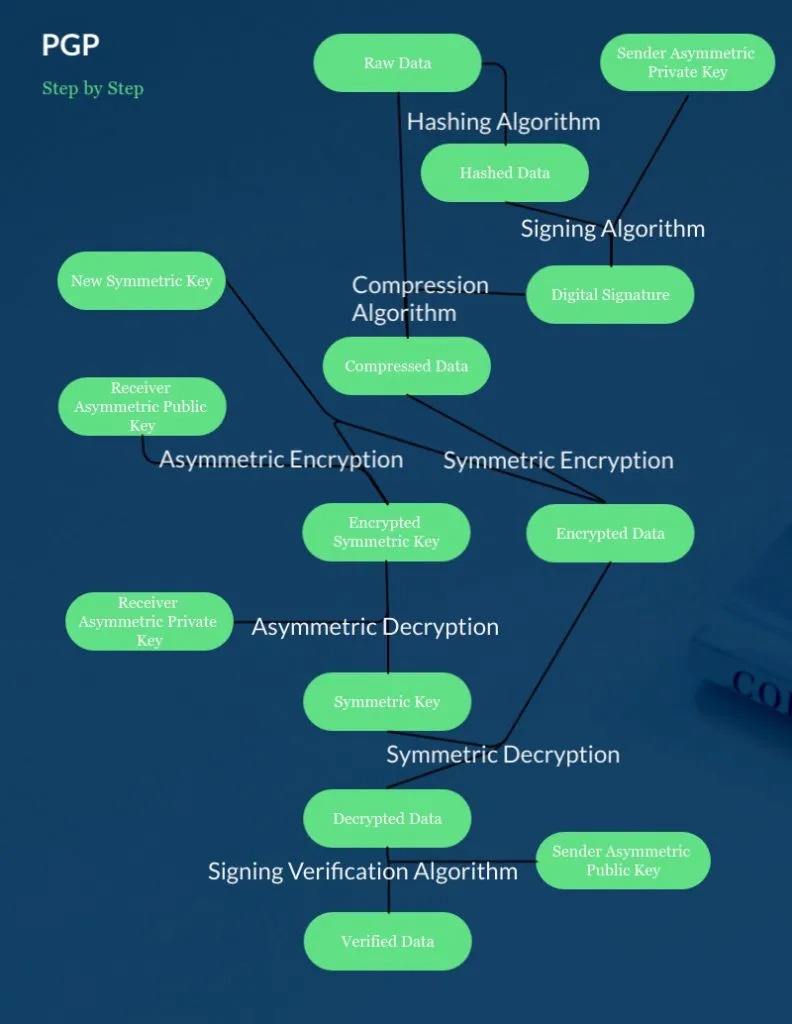
OpenPGP, the protocol to which PGP and GPG adhere, can really be looked at as a set of rules for how we use other encryption and authentication algorithms. There are four main components of a PGP system:
- Symmetric encryption
- Asymmetric encryption
- Hashing and Digital Signatures
- Compression
Putting It All Together 🔗
Let’s go through each step of how a PGP message exchange works:
- Raw data is hashed and signed using the sender’s asymmetric private key. This will allow the receiver to verify that the message is from who they think it is.
- The data is compressed to save space
- A new random symmetric key is generated for this exchange
- The random symmetric key is used to encrypt the compressed data
- The symmetric key is encrypted using the receiver’s asymmetric public key
- The encrypted symmetric key and the encrypted data are sent to the receiver
- The receiver uses their private key to decrypt the symmetric key
- The receiver uses the symmetric key to decrypt the data
- The data is decompressed
- The receiver verifies the digital signature using the sender’s public key
That’s it! If you have questions be sure to reach out on Twitter.
Which Algorithms are Used? 🔗
PGP defines in the official RFC 4880 which algorithms must and should be supported by PGP clients. Let’s go over each one.
Symmetric Encryption Algorithms: 🔗
Implementations MUST implement TripleDES.
Implementations SHOULD implement AES-128 and CAST5.
Implementations that interoperate with PGP 2.6 or earlier need to support IDEA, as that is the only symmetric cipher those versions use. Implementations MAY implement any other algorithm.
Asymmetric Encryption Algorithms: 🔗
Implementations MUST implement DS for signatures, and Elgamal for encryption.
Implementations SHOULD implement RSA keys.
RSA Encrypt-Only and RSA Sign-Only are deprecated and SHOULD NOT be generated but may be interpreted.
See section 13.8 for notes on Elliptic Curve, ECDSA, Elgamal Encrypt or Sign, and X9.42.
Implementations MAY implement any other algorithm.
Digital Signature Algorithms: 🔗
Implementations MUST implement SHA-1. Implementations MAY implement other algorithms. MD5 is deprecated.
Compression Algorithms: 🔗
Implementations MUST implement uncompressed data. Implementations SHOULD implement ZIP. Implementations MAY implement and other algorithms.